Bug bounty program
Security is a collaboration. Report bugs and be rewarded.
About Deriv
We provide online trading services to over 2 million clients via desktop and mobile applications across multiple platforms.
Security is important to us. We continuously improve our products and services by collaborating with independent security researchers worldwide.
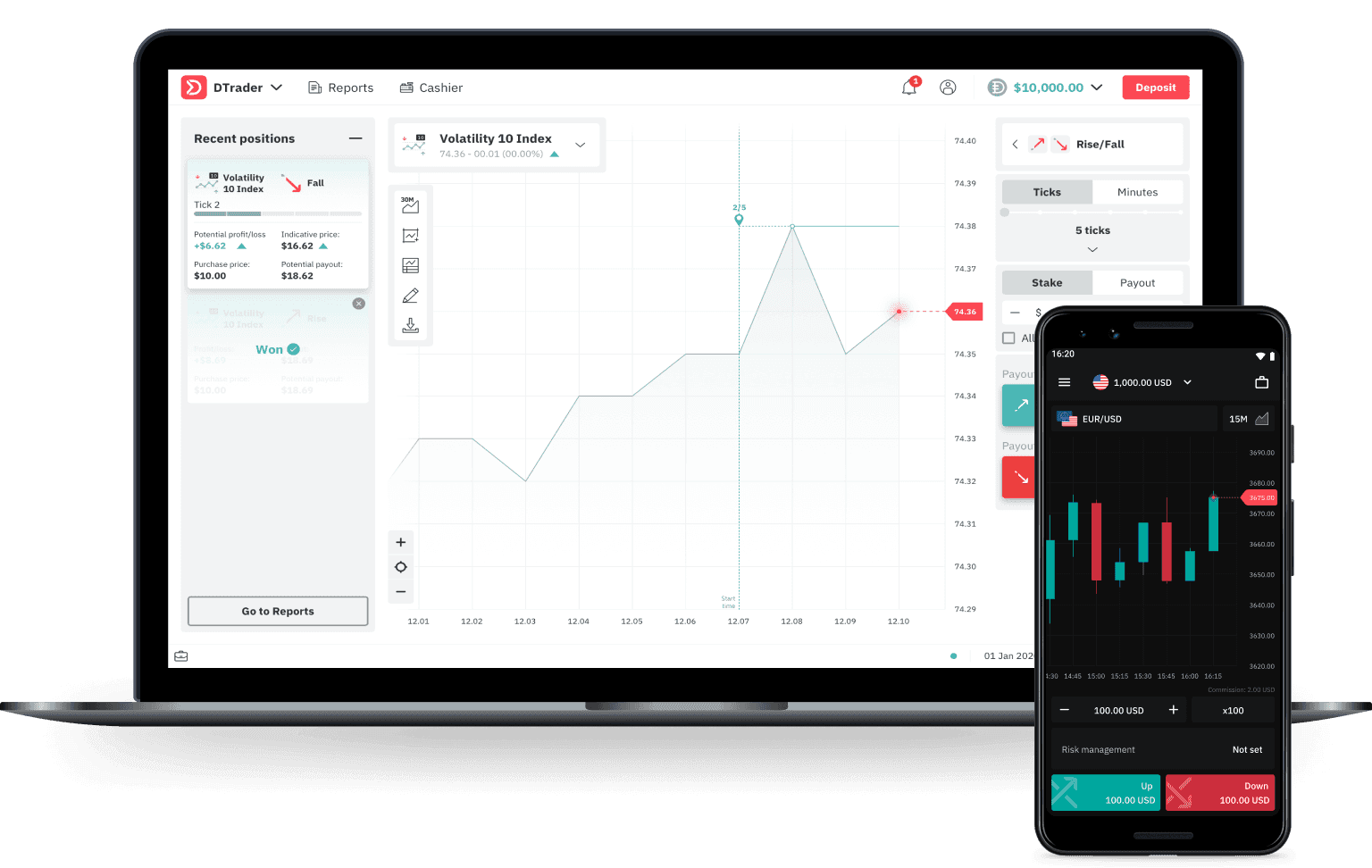
Scope
Only Deriv assets are covered in this program. If you discover bugs on third-party apps, please report them to the respective owners. You may submit bug reports related to the following aspects of our business:
Important businesses
Our payment site: cashier.deriv.com
Our login site: oauth.deriv.com
Our WebSockets API: *.binaryws.com api.deriv.com
Our main trading platform: app.deriv.com*
*This only covers the functionalities handled by Deriv
Our legacy trading platform: smarttrader.deriv.com
General businesses
Our GitHub repositories:
github.com/binary-com
Our CFD trading application by Devexperts: dx.deriv.com
Deriv P2P: Our peer-to-peer payments app (Android app, iOS app)
Deriv GO: Our options trading app (Android app, iOS app)
Deriv X: Our CFD trading app by DevExperts (Android app, iOS app)
Our site for marketing campaigns: trade.deriv.com (third-party)
Edge businesses
Our site for static resources: static.deriv.com
Our tracking site: t.deriv.com
Our FIX feed server for Deriv X: fix.deriv.com
Our internal apps: *.deriv.cloud
Our weblog address: https://blog.deriv.com/
The following third-party apps are not covered in this program:
Our charting site: tradingview.deriv.com
Our graduate programme site: besquare.deriv.com
Our CFD trading platform by MetaQuotes: metatraderweb.app
Our community site: community.deriv.com
Out of scope vulnerabilities
Clickjacking on pages with no sensitive actions
Cross-site request forgery (CSRF) on unauthenticated forms or forms with no sensitive actions
Attacks requiring man in the middle (MITM) or physical access to a user's device
Previously known vulnerable libraries without a working proof of concept (PoC)
Open redirect — unless an additional security impact can be demonstrated
Output from automated vulnerability scanners without a PoC to demonstrate a specific vulnerability